CodeTogether Security
It’s your code, you own it, and CodeTogether is fundamentally designed to keep it private. Here’s how:
- AES-GCM is used for end-to-end encryption of your data
- The encryption key is never shared with our server, it is only accessible by the host and participants
- SHA256-RSA encryption is used to securely transfer all data between the host, the CodeTogether backend, and participants
- CodeTogether does not transfer your project’s source to its servers, or any remote repository—it remains on your system
- Encrypted source of files being edited is relayed through the CodeTogether backend, the backend does not store, nor can it read this data
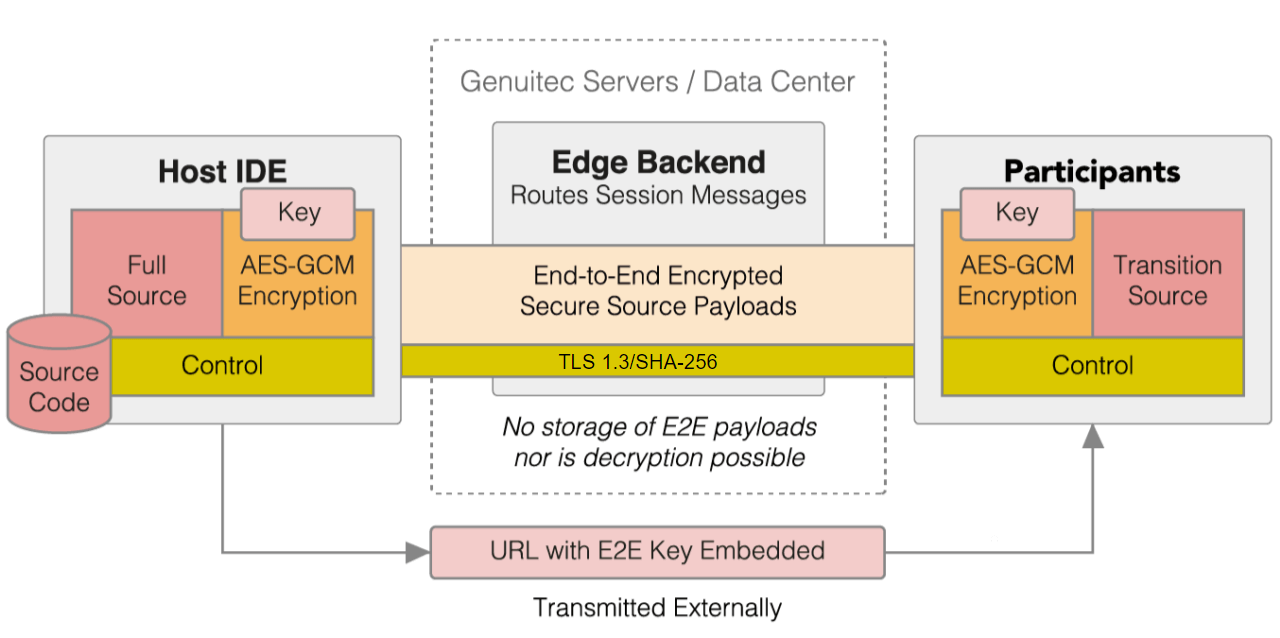
End-to-end encryption in CodeTogether
Encryption Details
When you start a CodeTogether session, a unique key is generated for the session. This key is used for AES-GCM encryption at the host and all participants. Our servers never receive this key. Even if our servers were to somehow be compromised, your data would remain protected because the attackers would not have the encryption key. The following diagram visualizes how the end-to-end encryption works.
Encryption of the Audio/Video Bridge
A/V communications use encrypted WebRTC channels that are independent from the CodeTogether session services discussed above. Due to limitations in how browsers currently support WebRTC, these communications are not end-to-end encrypted. In the unlikely event of these channels being compromised, as they are independent of the regular CodeTogether session, they can never expose access to the source code or your CodeTogether session in any way.
Full Source Stays on Your System
When a file is opened by the host or participants, its encrypted contents are relayed through CodeTogether servers. To provide functionality like code analysis, IntelliSense, search, or even editing, participants do not need to download the full repository to get assistance. Instead, CodeTogether relays efficient and specific functional requests to host systems. Not only does this make CodeTogether sessions very performant, it also minimizes the amount of source code that is transferred securely between systems.
CodeTogether servers never store relayed data. During a code sharing session, the only customer-identifiable information tracked on our servers is duration, and number of participants in sessions, which is used to enforce license levels. IP address information is tracked in connection logs.
How We Protect Your Data
The Edge backend server has the responsibility of routing requests between edge clients, whether hosts or participants. To do this, certain control information is passed to allow the correct routing of messages. For instance, if routing a selection operation, the edge server will route the message to all participants that are following the individual making the change. While the backend will know a select action is being performed, it will not know to which file. Similarly, all sensitive information is encrypted as part of end-to-end communications, including:
- Paths and filenames for source being edited
- Source content and source files
- Marker information including errors
- Content assistance information
- Hover and peek information
- Copy/paste bulk operations
- Search results
- And more
This same level of security can be hosted on your servers, behind your firewall, using the On-Premises version of CodeTogether.
Security Concerns and Questions
For commonly asked question, please refer to the Security section on our FAQ.
Security is our top priority. If you have any questions, concerns, or would like to report a potential security vulnerability, please reach out to us at security@codetogether.com.
